Improving Data Privacy Using Process Mining

Think quick: how many times do you share information about yourself each week, or even each day? When you consider how many times you submit your email address on various websites or enter other personal information anywhere else, it quickly becomes clear that it’s even more than you think.
Today, your online, digital security is just as important as keeping your doors locked at night, which means that all companies must do all they can to improve their cybersecurity efforts.
New regulations, a new focus on cybersecurity
Many governments and industries are now creating new laws and regulations to protect citizen and consumer data. For example, the European Union recently introduced the General Data Protection Regulation (GDPR) to create better data privacy controls for EU citizens. Faced with potentially huge fines, businesses of all sizes–and around the world–had to create new strategies to follow GDPR’s data privacy requirements.
This focus on cybersecurity has led us to a current scenario where just about any new software implementation now requires thorough evaluation from a security perspective. Clearly, it’s a top priority to prevent data breaches and the loss of confidential customer, employee, and corporate data. While there are so many specialized cybersecurity solutions and niche applications, it is important to make sure that enterprise systems and business process management (BPM) solutions, such as process mining, are secure.
This blog article will introduce the concept of process mining and take a closer look at what security aspects to consider when starting process mining initiatives.
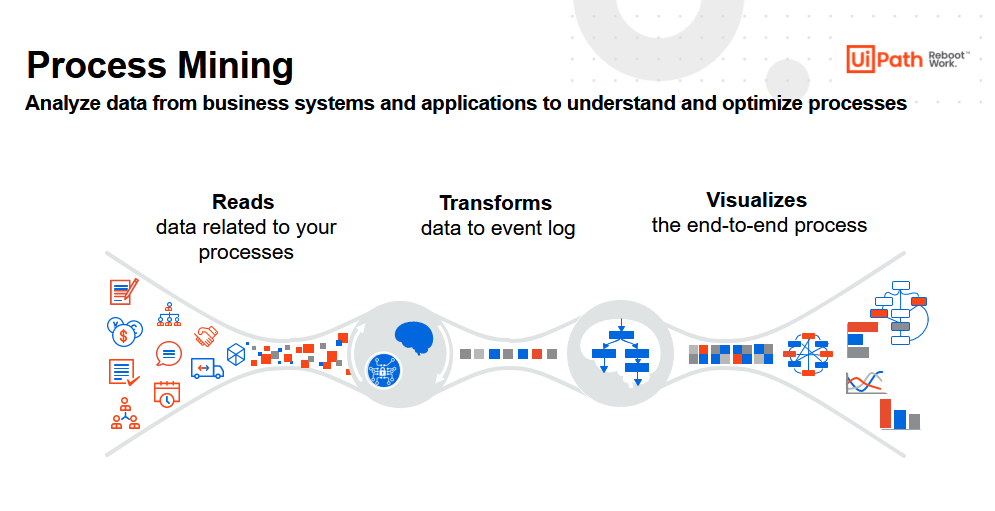
What is process mining?
Process mining is an innovative technology that enables users to build a reliable visual process based on a company’s digital activities. For example, as employees and software robots interact with corporate IT systems, their activities are captured by those systems. Process mining transforms this data into an event log and then creates new visualizations of the end-to-end process.
By examining any given process through a process mining tool, users can gain an entirely new perspective and valuable new insights. The result? Users have the insights needed to improve existing processes and enable better decision making. More specifically, companies can now use process mining to enhance internal efficiencies and reduce complexity. Both are critical first steps in positioning the organization to improve its approach to cybersecurity.
It is also worth mentioning that since process mining can be provided by third parties, who generally gain access to a company’s information during the process, it’s important to choose process mining providers with secure products and processes.
Teams should also take care to protect sensitive information every step of the way—even in areas that may not seem obvious. For example, process mining tools can show all the details about an employee’s work, so if one worker is not performing at a high level, this data should be encrypted. This way, the employee’s manager is the only one who sees this information and can work with the employee to improve these results.
Privacy by design
Before trying to use process mining to enhance cybersecurity (or any other process), users must start by thinking through the need for transparency and how to best optimize workflows and other outcomes. More specifically, they must consider:
The data they will need
How to extract that data
How to make sure this data is protected and meets compliance requirements through every step of the process
Since process mining tools work with corporate information, it can be challenging to keep the privacy of all stakeholders under control. The challenge is especially true when you consider that corporate data has employees’ and consumers’ personally identifiable information (PII), including the names, addresses, departments, user IDs, and much more.
The privacy by design principle focuses on striking the balance between providing transparent data and protecting stakeholders’ privacy. This engineering approach encourages technology providers to emphasize privacy before anything else. Thus, any privacy by design approach should treat privacy in a proactive, preventative manner before any other considerations related to any other workflow, process, or capability.

Privacy decisions to consider with process mining
To make sure that any new process does not conflict with personal data policies and does comply with requirements, there are a few points to consider:
Access to raw data: as the first step, carefully consider the overall data extraction process, whether it is from the company’s IT system or data warehouse. The process mining implementation team needs to have access to this corporate data, so they can focus on extracting what’s most important for analysis. As a result, it’s important for the company to choose the data it will grant access to for further analysis, a step that also helps accelerate and simplify the overall implementation.
Choose the right strategy: filter, pseudonymize, or anonymize data. After that, the process mining team needs to work on the translation of the raw data. They can convert this information into comprehensive terms and develop a format suitable for process mining. Ultimately, the data then gets transformed into dashboards that the team will use to decide what features to focus on.
At this point, there are three choices to managing personal information: filter, anonymize, or pseudonymize.
Filter: sometimes the company needs to track information that is not needed for specific process analysis. In this case, the team would simply recommend removing it. If the data is sensitive and does not influence the business analysis outcome, users can delete it, especially since the focus should be on valid and relevant data.
Pseudonymization: this is the most common way of handling sensitive data. Simply put, it’s a way of encrypting the information so that users can’t correlate it to real data–specific names, addresses, or other PII data.
In this case, the team can choose to replace any PII data with pseudonym information wherever possible. For example, if the company doesn’t want analysts to see the names of employees that perform process-related tasks. In this case, the team can replace these names with numbers. Only select users would be able to access the table of “translations” to identify the actual names.
Anonymization: this is nearly identical to the pseudonymization procedure where the team chose to replace PII data with unique pseudonym. But this time, there is not translation table. Thus, the original data is secure since re-anonymization impossible. But this time, there is no translation table. In this way, unauthorized users can’t identify individuals’ confidential information using the available data.
One consideration: anonymized data can complicate process analysis, especially if the company over-secures the data to the point that the end insights are not useful anymore.
Access to finalized data
When the data is ready and considered “final,” it is important to consider how the data will be accessed in the new context. The process mining team should define business users who will have access to dashboards, process graphs, reports, and other information.
The right process mining tools, such as UiPath Process Mining, deliver valuable self-service tools that give access to IT teams while still giving the ownership and control to business users. Both groups can work independently to a common goal: gaining new insights into existing processes.
Interested in learning more about process mining? Watch our video on UiPath Process Mining or download our white paper, Accelerating RPA with End-to-End Process Understanding and Monitoring today.
Topics:
Process Mining
Global Demand Generation Program Manager, UiPath
Get articles from automation experts in your inbox
SubscribeGet articles from automation experts in your inbox
Sign up today and we'll email you the newest articles every week.
Thank you for subscribing!
Thank you for subscribing! Each week, we'll send the best automation blog posts straight to your inbox.



