How to protect data with UiPath security features
Share at:

Introduction
In our increasingly digital world, protecting sensitive information is more important than ever, especially as more organizations turn to automation to improve efficiency. UiPath takes this responsibility seriously by incorporating a range of security measures to keep data safe and secure.
This article will take you through the essential elements of how to protect your data in UiPath automations. We'll explore how UiPath encrypts the data when it's being transmitted over networks and when it's stored, provided sensitive information remains confidential and intact. We'll also look at the role-based access control (RBAC) system, which helps manage who has access to what within the platform, and how UiPath integrates with existing enterprise identity management systems to streamline user management and enhance security.
By understanding these security features, organizations can confidently apply UiPath powerful ecosystem while keeping their data secure and complying with relevant regulations. Let's dive in and see how UiPath makes this possible.
Encryption
Encryption is a process used to protect sensitive information by converting it into a format that is unreadable to anyone who does not have the proper authorization or key to decrypt it. It involves using algorithms to transform plain text (human-readable data) into cipher text (an encoded version that looks like random characters). Regarding UiPath and its automations, there are two very important types of encryption that you should pay attention to too, in transit and at rest. Let’s deep-dive into both of them.
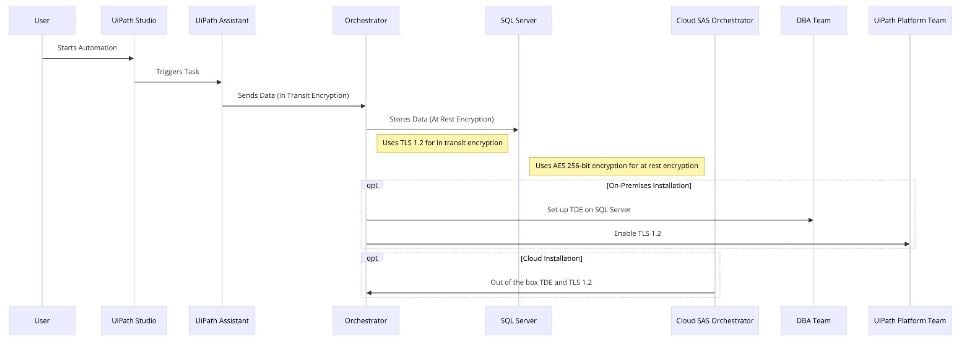
First, in-transit encryption. It refers to the process of encrypting data as it is being transmitted over a network to prevent unauthorized access and guarantee its security during transfer. This would include the traffic sent from the devices running the UiPath Studio and/or Assistant to the UiPath Orchestrator. These devices could be laptops, VDIs, VMs, and even servers running those software packages. The UiPath cloud uses TLS 1.2 by default, which is in line with industry standards. If you have an on-premises installation, your UiPath Platform team will most likely be the one responsible for the enablement of this feature.
For instance, imagine you're running an automation from your laptop. Depending on the logging settings you've chosen, this process may generate various logs that could range from mundane to sensitive data, all initially stored in plain text. However, here's where security steps up: as soon as these logs are transmitted from your laptop to the Orchestrator backend system, they're encrypted in transit. This means that if any unauthorized person tries to intercept this data during transmission, all they'll see is a jumble of unreadable characters. It's a seamless yet powerful safeguard that keeps your data secure every step of the way.
Running head-to-head with in-transit encryption is the at-rest encryption. As the name suggests, it involves securing data stored on a physical media, such as a hard drive or cloud storage, to protect it from unauthorized access and protect its confidentiality. The UiPath Platform uses MS SQL server database as its default storage. The default encryption for MS SQL Server is Transparent Data Encryption (TDE) which leverages AES 256-bit encryption. Once again, if you have an on-premises architecture, your DBA team will have to set that up on the UiPath SQL Server instance. On the other hand, this feature comes out of the box with the cloud SAS platform.
This diagram depicts the data workflow and where the encryption happens.
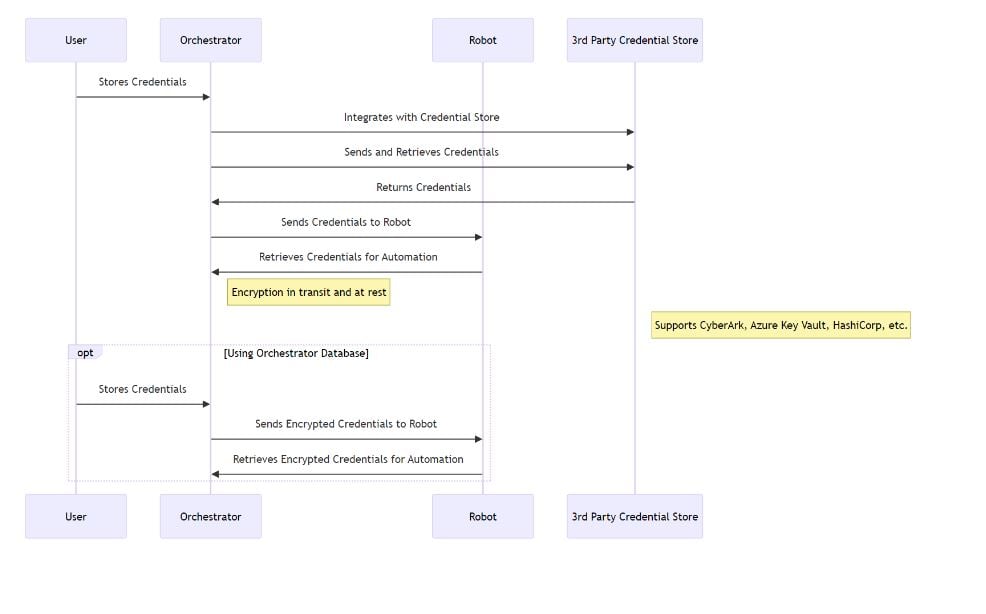
Secure credential management
Orchestrator enables users and robots to securely store secrets and credentials directly within the Orchestrator database. That’s due to the encryption in transit and at rest provided by the platform. It uses encrypted assets and credentials that can be securely retrieved by robots during automation execution. Nonetheless, for more critical solutions which require an external secured vault, the Orchestrator can be easily integrated with 3rd party credential stores such as CyberArk, Azure Key Vault, and HashiCorp.
Role-based access control (RBAC)
UiPath role-based access control (RBAC) is a security framework that restricts system access to authorized users based on their roles within an organization. It can be set up in such a way which provides that users have the necessary permissions to perform their job functions, enhancing security and simplifying management. By assigning specific roles to users, RBAC helps in enforcing the principle of separation of duties. This reduces the risk of fraud or errors, as no single user has control over all aspects of a process.
The Orchestrator includes a predefined set of roles designed to offer customers a foundational framework for managing their automation program. These default roles simplify the initial setup and help provide that users can quickly start leveraging the Orchestrator capabilities. However, the Orchestrator is highly adaptable, allowing administrators to customize these existing roles to better fit the unique needs and workflows of their organization. Additionally, administrators can create entirely new roles from scratch, making sure that the role definitions align perfectly with their organization's specific policies, procedures, and individual job responsibilities. This flexibility provides that the Orchestrator can be tailored to support a wide variety of organizational structures and operational requirements.
UiPath Orchestrator is also designed to seamlessly integrate with existing enterprise identity management systems, such as Microsoft Active directory, Google, Windows, Azure AD, and PingFed. This integration allows organizations to manage user identities and access permissions from a centralized location, providing consistency and security across all platforms. By leveraging this integration, administrators can streamline the process of granting and revoking access to the UiPath Platform, reducing the complexity and potential for errors associated with managing user permissions manually.
Protecting sensitive information
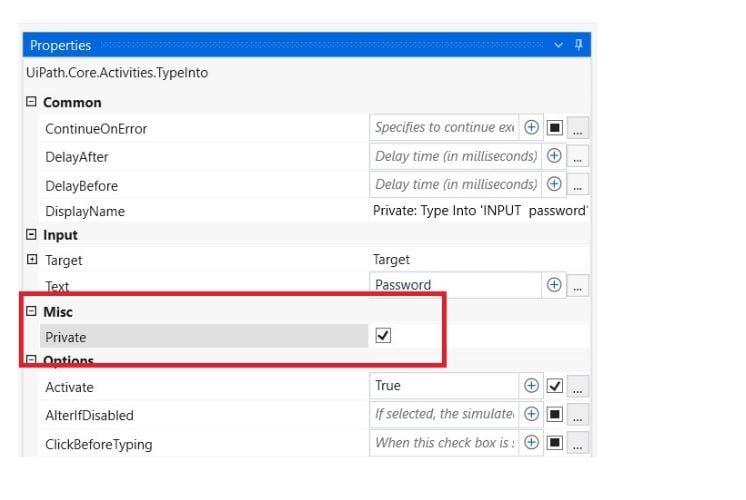
UiPath has a set of robust features to ensure that sensitive information is protected throughout the automation process. For instance, protecting sensitive information can be achieved during automation development. Developers can control what data is logged by selecting the 'Private' property in activity properties, which prevents the logging of sensitive data like passwords, personal information, or even credit card numbers. This approach helps in minimizing the risk of sensitive data leaks during debugging or while running automations in production environments. This helps secure and maintain compliance with data protection regulations.
Another key feature is data masking, which allows developers to obscure sensitive data so that it is not exposed during the execution of an automation workflow. This is particularly useful for preventing confidential information, such as personal identifiers, financial details, or proprietary business data, from being displayed for users, or captured on screenshots and videos that are generated during the automation process. This feature is essential for organizations that need to comply with strict data protection regulations, such as PCI, GDPR, or HIPAA, as it minimizes the risk of data breaches and unauthorized access.
Additionally, UiPath provides a set of cryptographic activities designed to enhance security by allowing developers to securely handle and protect sensitive data during automation workflows. These activities enable encryption, decryption, hashing, and other cryptographic operations, providing data integrity and confidentiality.
Conclusion
UiPath comprehensive security measures for protecting sensitive information in automation projects are crucial for maintaining data integrity and confidentiality. By employing robust encryption protocols for data both in transit and at rest, integrating secure credential management, and implementing a flexible Role-Based Access Control (RBAC) system, UiPath makes sure that sensitive data is well-guarded against unauthorized access. These features, combined with seamless integration with existing enterprise identity management systems and advanced data masking capabilities, enable organizations to leverage automation confidently while adhering to stringent data protection regulations. As a result, UiPath enhances operational efficiency and provides a secure foundation for the evolving digital landscape.
TopicsLABEL.text
Orchestrator
UiPath Enterprise Product Owner/Technical Lead, TD Bank
Get articles from automation experts in your inbox
SubscribeGet articles from automation experts in your inbox
Sign up today and we'll email you the newest articles every week.
Thank you for subscribing!
Thank you for subscribing! Each week, we'll send the best automation blog posts straight to your inbox.



